G0X Labs
At G0X Labs, we unlock the secrets of digital shadows. Enter if you dare, but tread carefully—every keystroke echoes through the grid. Prepare to venture beyond ordinary boundaries and explore the core of online security and hidden pathways.
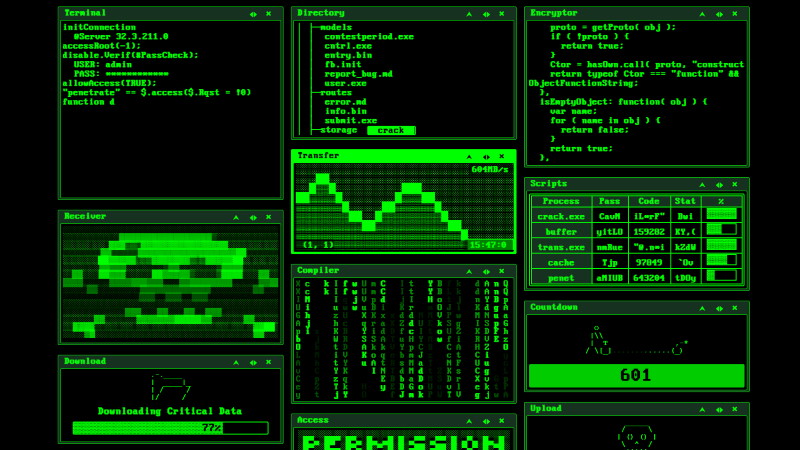
This immersive experience is not just any hacker simulation; it’s a portal to the unseen. With ASCII visuals and cryptic screens, G0X Labs offers the realism you crave. Explore, toggle, expand. Your journey through our corridors is as dynamic as the dark web itself.
Configure
At the “Start” point, tune your portal—choose your visual scheme: monochrome, retro green, or something dark. Set the pace, adjust the font, resize the windows to echo the pulse of your monitor. Stay in control or let the screen flow.
Secret Codes
Numbers lead to secrets. Press any digit and unveil encrypted commands. The system responds with the mystery you seek.
Portals and Gates
- Terminal - Watch the cursor blink. Type anything; the screen will respond with code as if alive.
- Directory - Traverse through a system’s spine; watch each folder crack open in a rhythmic beat.
- Encryptor - Code appears line by line, like layers being stripped away.
- Transfer - Observe the shifting pulse of data, speed flashing in an endless stream.
- Scripts - The random, the unknown—data tables filled with cryptic entries.
- Receiver - Distorted images hint at the forbidden. Tap into the unknown, but beware of what might answer.
- Compiler - Code rains in green; the matrix lives here.
- Download - Progress unfolds like a signal drawing you in.
- Upload - The digital dark’s malware stream, inching towards completion.
- Access - Green light flashes; entry permitted. Beware the key’s twist.
- Warning 1 - Access denied; the path blocked by an unseen hand.
- Warning 2 - “Top Secret”—some things are better left untouched.
- Help - This screen—perhaps your only guide in the labyrinth.
Guard Against the Shadows
The only secure system is a disconnected system. Yet, for those who dare, follow these whispers:
- Unique access only—one password, one gate. Sequences like “1234” are open invitations.
- Fortify passwords with chaos. Numbers, symbols, and broken phrases guard best.
- Stay alert for echoes—activate dual verification; be notified of suspicious entries.
- Refresh systems frequently. Trust nothing, verify everything.
- Freeware often bears a hidden cost. Use only trusted sources.
- Customize installs; avoid “recommended” paths—they bring unwanted shadows.
- Log out. Disconnect. Clear traces when your work is done.
- Only secure files on devices you control; prying eyes leave few traces.
- Encrypt everything, trust HTTPS paths.
- Activate firewalls; third-party shields can be both friend and foe.
- Beware of phishing—hidden traps that mimic familiar faces.
- Consider multiple identities; don’t leave all doors open.
- Check privacy; keep only what you truly need accessible.
- Lock your physical world—PINs, patterns, face ID. Have an escape plan.
- Avoid open networks; secure your own stronghold.
- A VPN disguises you; use it as your digital armor.
- If hacked, remain calm—lock your doors, alert only the trusted.
- Trust nothing; question everything. Here, suspicion is survival.